
TechSoup is working hard to ensure the security of our website, and most importantly, the security of our members' information. We have recently put in place a new security measure called Transport Layer Security 1.2 (TLS 1.2) that helps with that. TLS is a type of HTTPS encryption. We like it so much that we recommend you also add TLS encryption to your nonprofit website if you are collecting any sensitive data, such as donation information.
How This Affects You When You Use TechSoup
Starting on June 26, 2018, please make sure that you are using the latest version of your browser when using the TechSoup website. If you need to update your browser, here are links for Chrome, Firefox, Safari, Microsoft Edge, and Internet Explorer. If you don't have a current browser, you'll get an error message, and you won't be able to complete any donation requests.
TechSoup cares about your personal data. In our ongoing effort to protect it, we have released updates that enforce stronger encryption standards when processing information on TechSoup.org.
What Is TLS 1.2 and What Does It Do?
TLS 1.2 makes your information and transactions on the TechSoup site more secure. All payment processors are requiring that websites (like TechSoup's) that collect money have this new security measure in place.
TLS 1.2 is the newest and strongest form of encryption technology for websites. Websites around the world are switching to this new protocol to ensure better security for people using their site. TechSoup enabled TLS 1.2 on our web servers so that online transactions and confidential data relayed between your web browser and our website is encrypted using the best protocol available. This protects your sensitive information when you place product donation requests.
Here's a table that helps explain the difference between having TLS and not having it.
| TLS Protection | No TLS Protection | |
|---|---|---|
| BROWSING | Your web activity is only visible by people at your destination website. Even if someone intercepted your message or traffic, it would be scrambled. | Anyone along the way can see exactly what you're doing on the web. If someone intercepted your message or traffic, it could be read. |
| HOSTING | Only your authorized staff can access donor or private information. Passwords used to access hosted sites are encrypted better. | Donors and anyone entering private information on your website are much more liable to have their information stolen. Data that is entered into forms can be read if intercepted. |
Here's an infographic that explains more about HTTPS.
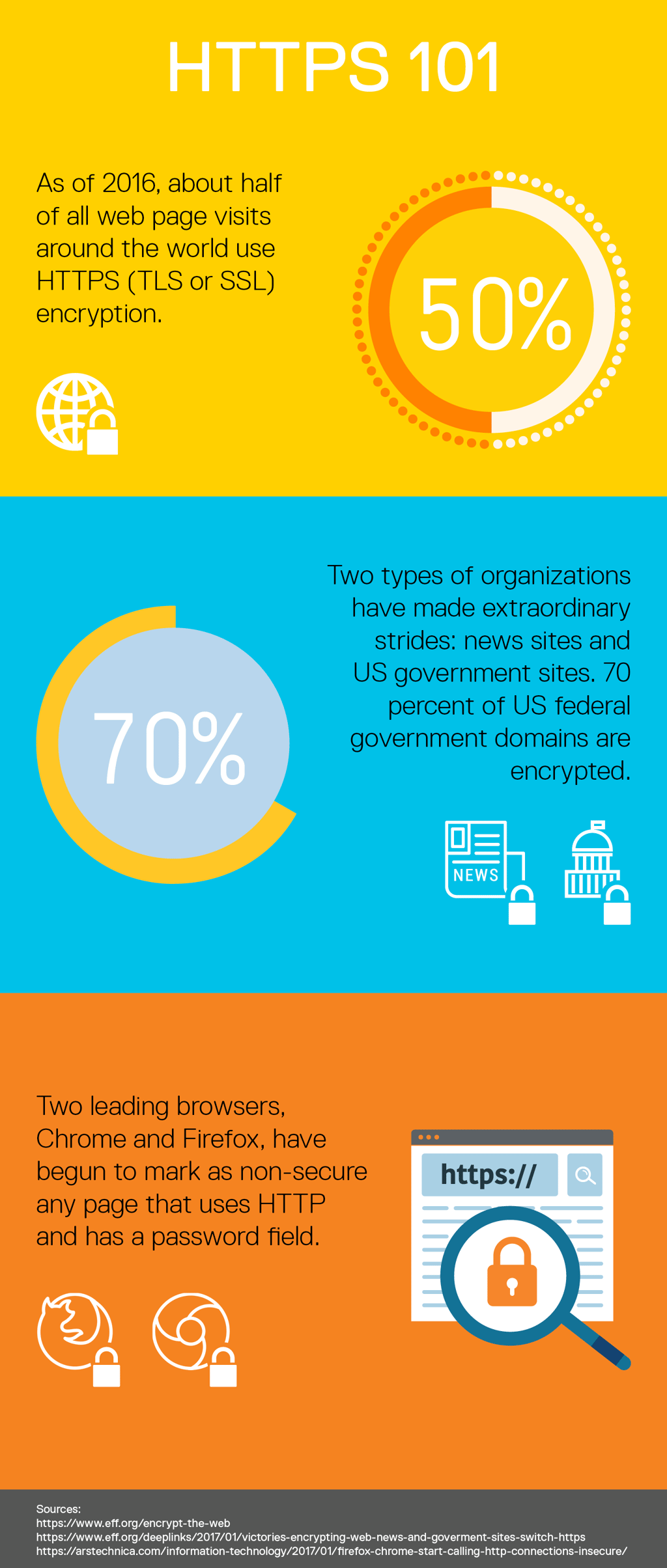
A secured web page can be identified by a padlock symbol at the bottom of the browser window or in the address bar. We are working on making all of our pages secure in the coming months.
Which Organizations Especially Need TLS 1.2 Protection?
Any website can benefit from having TLS 1.2 protection, but the following types of sites especially need it.
- Organizations that collect, store, or process payment information, such as donor credit card numbers, on their website.
- Organizations that collect sensitive client information on their website. This is especially important for any type of medical information.
- Organizations that transmit data over the Internet from one website to another.
How Your Organization Can Upgrade to TLS 1.2 on Your Website
The TLS protocol replaces an older security protocol called Secure Sockets Layer (SSL). If your website uses SSL or no security protocol at all, we recommend that you implement TLS 1.2 on your website. Here's how to do that.
- You will probably need an IT person familiar with your web server software or web hosting service to configure things so that your website is properly set up for TLS.
- Purchase a digital certificate from a certificate authority. This is independent of the upgrade to the new protocol.
- Three certificate authorities, Symantec, Comodo, and GoDaddy (all are TechSoup donor partners), account for three-quarters of all certificates for TLS on public-facing web servers. Comodo provides security certificates as product donations through TechSoup. (Editor's note: Comodo's security certificates are built on TLS, even though Comodo continues to label them as SSL.)
- There are nonprofits that issue digital certificates without charge like CAcert and Let's Encrypt.
- If you manage your website entirely through a web hosting provider, many hosting providers already integrate Let's Encrypt support as a setting you can turn on.
- Older protocols such as SSL2 and SSL3 should be removed.
- To test your webserver's use of security protocols, you can use the free GlobalSign tool.
TLS is not a magic bullet. Implementing it or any other single security measure will not fully protect your organization from data breaches, but implementing the TLS security protocols is a major tool in reducing the chance of cybercrime on your website.
Additional Resources
- Find out more about keeping payment information secure.
- If your organization collects sensitive health information, you may want to check out our article, In Search of HIPAA-Compliant Software.
- Learn more about the future of security threats.
- Check out our recent blog post on how to lock down your data and protect yourself.








