This blog post is more than five years old. It may contain outdated information or refer to products that are no longer available.
As organizations increase the use of remote work tools, Zoom usage has skyrocketed. With this, some basic flaws in Zoom's native and default security have come to light, along with increased concern over privacy. In response to this, Zoom has worked to improve its security and privacy policies.
For most usage, Zoom is safe. However, there may be times when it is necessary to gauge the sensitivity of the content of the meeting and either configure Zoom to be more secure or choose another tool altogether. Below are some ways to configure Zoom for particular use cases.
Use the guide below to configure your Zoom account to both maximize your privacy and optimize your experience for different types of remote meetings at your nonprofit.
Open Meeting — No Sensitive Information Shared
If you are using Zoom for an open discussion and would like to make attendance as easy as possible, the default security settings should be appropriate. You should also have high confidence that there will be no sensitive information shared.
Board Meeting, Team Meeting, Private or Confidential Meeting — Sensitive Information Shared
If a meeting might result in sensitive content being shared in either the presentation or the chat window, we would recommend that you enable the following security features:
- When you schedule the meeting, check to be sure that you have required a password and that only the expected participants are sent this password.
-
Expand the Advanced Options section at the bottom of the meeting scheduler. Ensure that you have configured the meeting to require the participants to authenticate and log in to Zoom. If they do not have a Zoom account, they will be asked to create a free account.
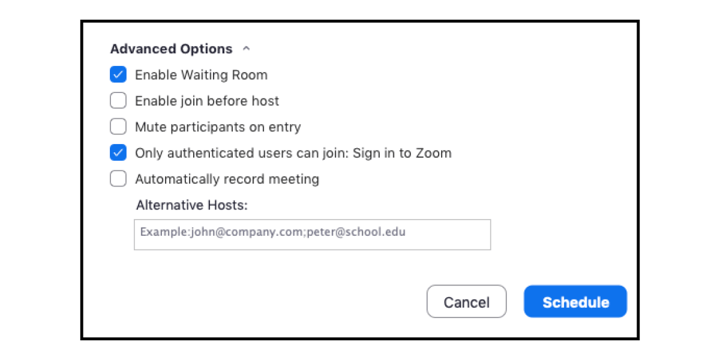
- Also in the Advanced Options area, you will be able to enable a "waiting room." This will allow you to view participants who have joined and then allow them into the meeting.
- Another feature in the Advanced Options area is to require the host to join first. This will ensure that the host can manage the participants as they join the meeting. In this case, it might be good to add alternative hosts.
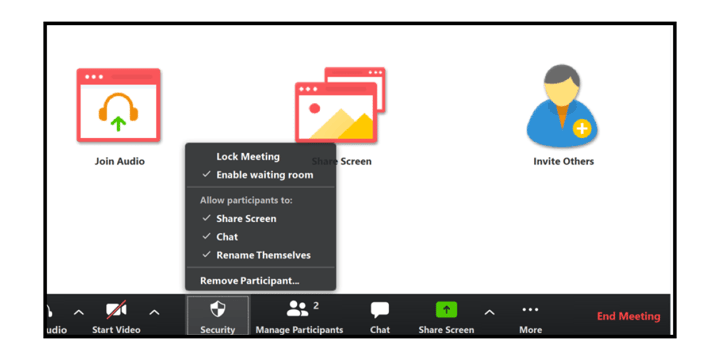
- After you have started the meeting and you have the expected participants in it, lock the meeting from the Manage Participants panel. This will keep others from joining.
-
Once the meeting has started, you might not want to allow others to share their screen, to chat, or to rename themselves. Zoom just released a new feature for hosts with the introduction of a Security button on the toolbar. When it is clicked, hosts can restrict those activities and set other security options.
- Your administrator will be able to turn on the Require Encryption for 3rd Party Endpoints (H323/SIP) feature in the settings section of the admin console. If your organization uses Zoom's Conference Room Connector, an add-on service, it ensures that if Zoom is used with other third-party Voice over Internet Protocol (VoIP) devices, such as conference room phones, the data will be encrypted end to end. Note that the device needs to be configured as well to enable this.
For team meetings, it would be appropriate to enable the same settings listed above, with the exception of enabling the waiting room and requiring the host to join first. This way, the members can begin the meeting before the host joins the call. However, if this team will be discussing sensitive information — for example, employees' personal information — it would be prudent to follow all of the same guidelines above.
Volunteer Meeting
If you are using Zoom with volunteers and are confident that there will be no sensitive information shared in the meeting, the default security settings should be appropriate. In this case, however, we recommend that you require a password.
Recorded Meetings
If you intend to record your meeting, you have the option to save the recording to your device or save it in the cloud. You can only save in the cloud with a paid account. You can configure the recording to be password-protected or available only to those in the same account. If you are concerned about the sensitivity of the content, you should consider both of these features.
When You Should Not Use Zoom
Zoom's standard encryption and other security features do not make Zoom appropriate for sharing content or data that, if breached, could be harmful for your organization's systems or have consequences for your constituents. Without additional measures — such as those available in the Zoom for Healthcare plan — and professional security auditing, Zoom should not be used to share data such as passwords, personally identifiable information, confidential client data, or medical records.








