Email spam is the unwanted gift that keeps on giving, inundating the inboxes of millions of charities and civil service organizations every day. The definition of a spam email is any message that is unsolicited. Also called junk mail, spam is often sent for commercial purposes. As a result, major laws have been set up to combat it, including GDPR, the United States CAN-SPAM Act, and Canada's anti-spam legislation (CASL).
But what can be done to stop the flood? Unfortunately not much. However, you can learn to spot spam when it arrives to help mitigate any IT threats that may occur as a result of opening an unwanted email.

Why Is Spam So Common?
Today there are millions of insecure computers and devices (PDF) connected to the Internet, giving spammers countless opportunities to fill unsuspecting inboxes. Their motives are diverse, ranging from financial fraud to Ponzi schemes.
While spam can come in many forms, this post will specifically cover how nonprofits can combat spam emails, drawing upon advice from Patrick Yokley, the information systems and operations manager at TechSoup.
What Is the Difference Between Spam and Phishing?
Phishing emails are a type of spam that "fishes" for sensitive information from individuals or entire organizations. These messages often mine for financial information and other critical data such as medical records and trade secrets. Criminals use a variety of phishing techniques, but the goal is always the same — to get a person to give up private information for malicious purposes.
Telltale Signs of Spam
1. Unknown Senders
Recipients of spam emails might be copied in a mass email from a person that supposedly interacted with them before. This spamming technique is called social engineering. If you have no idea who sent a message, just mark it as spam and definitely do not pass it on!
Here is an example of social engineering from Gmail:
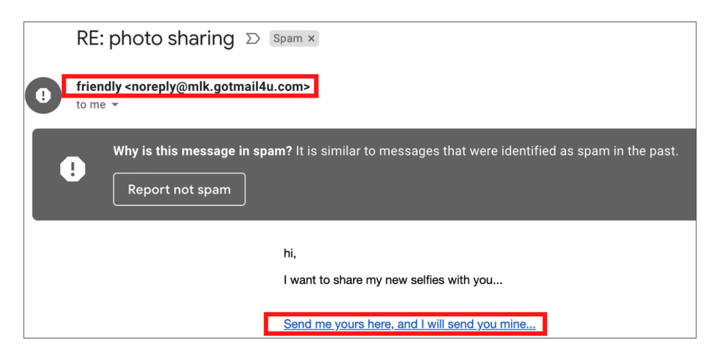
This message prompts the user to click on a potentially fraudulent link, and the sender has not identified themselves in any way.
Spammers may also use an alias to mask their real email provider in the sender line of a message. Below is a suspicious-looking sender, "Maureen Smith" at qq.com, that appeared in the To field when the recipient clicked Reply.
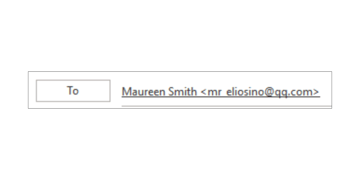
The domain qq.com turns out to be a chat service provider in China. While unexpected emails from other countries are not always a sign of spam, they provide an immediate red flag and warrant further investigation.
You can learn more about a message by checking the email headers.
Outlook
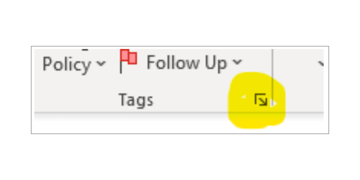
In Outlook, you can select the More Dialog Box Launcher button on the ribbon arrow at the side of the Tags box to open Properties.
Gmail
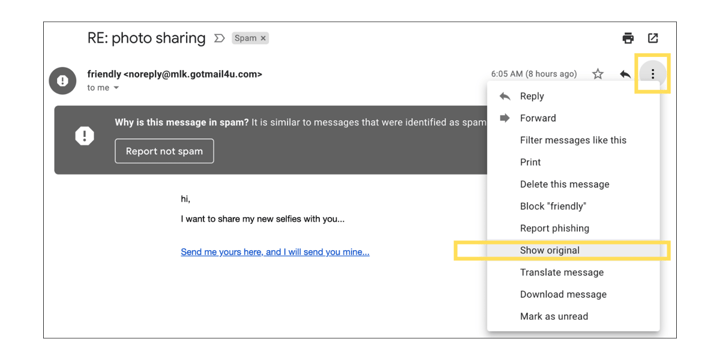
In Gmail, you can choose More > Show Original. The More menu is labeled with vertical dots next to Reply.
Message Header Tool
Google offers a Message Header tool that can pick out key information from message headers, such as whether the message passes or fails the three server verification methods. Paste the header into the box and click the ANALYZE button.
In addition to checking email headers, you can use a Reverse DNS/Whois Lookup to test if a sender is legitimate. Simply enter the domain name of the sender on https://whois.domaintools.com.
2. Bad Timing and False Alerts
Spam emails may stoke a false sense of urgency to coerce recipients to take unwarranted actions. Always refrain from taking any immediate action when encountering a suspicious message and contact an expert immediately.
The timing of a spam message may also be off. Any transactions that you cannot recall or those that did not occur within typical business hours are suspect. Other common warning signs include unexpected invoices, large file transfers, and access requests outside of the working week.
3. Suspicious Files and Attachments
Unfamiliar PDFs, zip files, and executables should never be downloaded. These types of attachments may contain programs that could compromise your device and network.
Links and buttons that go to insecure attachments and fake websites are also common. Hover your mouse over any URL before you click.
4. Spelling Mistakes and Bad Branding
Sloppy code, bad grammar, and formatting that looks off-brand are all hallmarks of spam. Other warning signs include embedded forms asking for personal information within an email or pop-up box.
A verified sender has explicit permission to email you in the first place, so a sure sign of spam is the absence of an opt-out option.
Reporting Spam
You can unsubscribe from receiving further communications from a spammer by simply marking a message as spam. For repeat offenders, create an email filter.
And if spam still continues, contact your IT expert to stop junk messages before they reach your inbox. These solutions could include applying role-based-access controls and enforcing multi-factor authentication — as well as updated antivirus and spam analysis software.
Trends in Spam
As millions of people around the world move to remote work, spam is on the rise — from pay-for-play schemes to cryptocurrency fraud to online dating. Some offenders are even exploiting social crises and natural disasters.
Think Before You Browse
Read the entire policy for any websites you visit to prevent unwanted use of your personal data.
You can also alert a spammer's webmail provider or ISP and submit a support ticket about the organization on SenderBase, the largest email monitoring network in the world.
Network Wisely
Limit how often your work and personal email addresses are publicly listed. Ask online networking groups and directories to take your information down and create a "junk email address" for online shopping and browsing.
Finally, update passwords throughout the year, storing them in a secure location.
While the above considerations might not prevent spam from entering your inbox entirely, they may at least help to prevent an unwanted cyberattack as a result.
Additional Resources
- Sign up for TechSoup Courses' Cybersecurity Bundle.
- See how to Manage Identities, Not Passwords at Your Nonprofit.
- Check out Nonprofits Beware: You Can Get Hacked Too.
- Watch the webinar Nonprofit Security Best Practices: Are They Out to Get You?








